Security News: Remote opens the gates, high watt botnets manipulated
7. August 2020Security News: Remote opens the gates, high watt botnets manipulated
Open barn doors instead of intelligent hacker killers – this is our conclusion again and again when we compile the news on this topic. One is also inclined to state that hackers are always one or more steps ahead of their hunters. This is also a fact: hardly any hacker becomes a hunter, while many hunters change sides. Why? Let’s speculate: 1. as a hacker, if you don’t play dumb, you hardly have anything to fear. Two: As a hacker, you can become a millionaire. 3. as a hunter you get grey hair early on and are more frustrated every year because you keep missing the mark.
What do you think has to happen to stop the hacker monster?
Write to us!
Plain text user names online
Plain text usernames, passwords and IP addresses for over 900 Pulse Secure VPN corporate servers were recently published online by a Russian hacker. The hacked Pulse Secure VPN servers were running a version of the firmware with a bug that exposed the servers to remote attacks. The hacker compiled the information between June 24 and July 8.
The leaked information included the firmware version of the Pulse Secure VPN server, SSH keys for each server, the list of local users and their password hashes, details of administrator accounts, and VPN session cookies.
Pulse Secure VPN Servers are typically used as access gateways to corporate networks to allow employees to remotely access internal applications.
The attacker posted the information in a Russian-language hacker forum.
Design flaw in Microsoft
Attackers use the Microsoft Teams Updater to retrieve and execute malware from a remote location. Microsoft has categorized this as a design flaw and is unlikely to fix it because it would affect the customers‘ operations.
Trustwave researcher Reegun Jayapaul said that privileged access is not required to exploit the bug because the installation is done in the Appdata folder of the local user.
Jayapaul believes that attackers could use the updater bug to hide their traffic.
The exploit method uses the teams‘ updater command to execute arbitrary binary code in the context of the current user.
Remote opens the gates
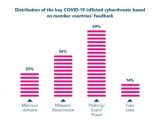
According to a recent analysis by Interpol, cybercriminals have shifted their targets to large corporations, governments and critical infrastructure (CI) during the COVID 19 pandemic.
These attackers are taking advantage of vulnerabilities created by the shift to remote work. The result: they steal data and cause various disruptions.
In addition, between January and April this year, a private security partner of Interpol discovered 907,000 spam messages, 737 malware incidents and 48,000 malicious URLs.
About two-thirds of Interpol member countries reported significant use of COVID-19 issues for phishing and online fraud.
April saw an increase in ransom – attacks – from threat groups that had been relatively inactive in recent months.
Malicious domain names
Attackers have lately increasingly used malware to collect data such as remote access Trojans, info stealers, spyware and banking Trojans.
Between February and March, the registration of malicious domain names increased by 569%. The majority relied on the key words „coronavirus“ and „COVID.“
Manipulated high watt botnets
Researchers at the Georgia Institute of Technology have discovered the trail of attackers who use high watt Internet of Things (IoT) botnets to manipulate the energy market. High watt IoT devices include stoves, air conditioners, and water and space heaters. According to the researchers, the hackers could, for example, trigger an increase or decrease in energy prices, buy energy when the price is low and sell it when it is high.
The method is not entirely new, as researchers in Princeton have already discovered a number of types of attack in 2018 that use high-performance IT to disrupt the energy network. These include attacks:
► leading to frequency instability
►einen Interrupt restart of the power grid
► Causing line failures and leading to cascade failures
► lead to the release of connecting lines
► increase operating costs
Attack with DNA exfiltrator
The Iranian hacker group APT 34 (aka, OilRig) is one of the first threat actors to have made the DNS-over-HTTPS (DoH) protocol a weapon.
Vincente Diaz, an analyst at Kaspersky Lab, said the group began exploiting the DoH protocol in May when it added DNA exfiltrator to its attack toolkit. DNSExfiltrator is an open source utility that establishes covert communication channels by hiding data in non-standard protocols such as the DoH protocol.
APT 34 targets financial, government, energy, chemical, and telecommunications organizations in the Middle East.
The group has previously used DNS tunneling to steal data from targets. Example:
Earlier this year, APT 34 carried out malware attacks against Westat, a company that works closely with the U.S. government.